Внимание
Мы работаем в штатном режиме. Наши склады готовы поставлять оборудование клиентам из Российской Федерации несмотря на санкционные запреты ЕС и США. Оборудование в РФ ввозится легально благодаря новому законодательству с параллельным импортом. Звоните и уточняйте! Информация актуальна на 18.12.25В связи с участившимися случаями недобросовестной конкуренции обращаем ваше внимание, что мы не передаем персональные данные третьим лицам
Поиск по сайту
Межсетевой экран Palo Alto PA-220
Почему нет цен?
Уточнить ценуГарантия до 5 лет
Диагностика перед отправкой
С нами выгодно и удобно!
- Поддержка персонального менеджера
- Партнёрские скидки до 70%
- Онлайн-кабинет гарантийного сервиса
Как купить?
Раз, два и все делаРассчитаем стоимость
Присылайте спецификацию для подбора и расчета стоимости оборудования
Привезём и подключим
Подключим и настроим оборудование в вашем офисе или ЦОДе
Характеристики
Отсрочка платежа
В зависимости от суммы поставляемого товара можем предоставить отсрочку платежа на срок от 5 до 90 дней. Условия отсрочки платежа рассматриваются индивидуально. Подробную информацию уточняйте у вашего менеджера.
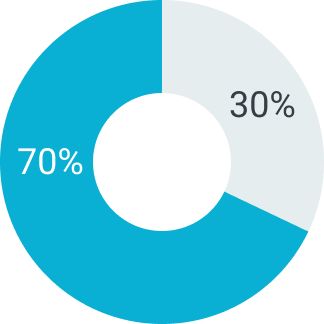
Первый платеж
Второй платеж
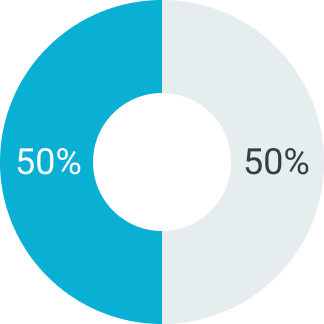
Первый платеж
Второй платеж
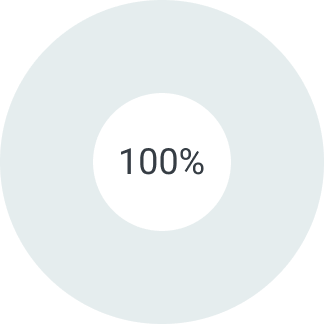
Первый платеж
Второй платеж
Описание
The controlling element of the Palo Alto Networks® PA-220 is PAN-OS® security operating system, which natively classifies all traffic, inclusive of applications, threats and content, and then ties that traffic to the user, regardless of location or device type. The application, content and user – in other words, the business elements that run your business – are then used as the basis of your security policies, resulting in an improved security posture and a reduction in incident response time.
Quick Specs
Table 1 shows the Quick Specs.
| Part number | PAN-PA-220 |
| Description | Palo Alto Networks PA-220, Security appliance, 550 Gbps firewall throughput, 270 Gbps threat prevention throughput |
| Firewall throughput (App-ID enabled) | 500 Mbps |
| Threat prevention throughput | 150 Mbps |
| IPSec VPN throughput | 100 Mbps |
| New sessions per second | 4,200 |
| Max sessions | 64,000 |
Product Details
Features1.Classifies all applications, on all ports, all the time
-Identifies the application, regardless of port, encryption (SSL or SSH), or evasive technique employed.
-Uses the application, not the port, as the basis for all of your safe enablement policy decisions: allow, deny, schedule, inspect and apply traffic-shaping.
-Categorizes unidentified applications for policy control, threat forensics or App-ID™ application identification technology development.
-Deploys consistent policies to local and remote users running on the Windows, Mac OS X, Linux, Android, or Apple iOS platforms.
-Enables agentless integration with Microsoft Active Directory and Terminal Services, LDAP, Novell eDirectory and Citrix.
-Easily integrates your firewall policies with 802.1X wireless, proxies, NAC solutions, and any other source of user identity information.
-Blocks a range of known threats, including exploits, malware and spyware, across all ports, regardless of common threat-evasion tactics employed.
-Limits the unauthorized transfer of files and sensitive data, and safely enables non-work-related web surfing.
-Identifies unknown malware, analyzes it based on hundreds of malicious behaviors, and then automatically creates and delivers protection.
Highlights
-High availability with active/active and active/passive modes
-Redundant power input for increased reliability
-Fan-less design
-Simplified deployments of large numbers of firewalls through USB
Compare to Similar Items
Table 2 shows the comparison.
| Model | PAN-PA-220 | |
| Firewall throughput (App-ID enabled) | 500 Mbps | 500 Mbps |
| Threat prevention throughput | 150 Mbps | 150 Mbps |
| IPSec VPN throughput | 100 Mbps | 100 Mbps |
| New sessions per second | 4,200 | 4,200 |
| Max sessions | 64,000 | 64,000 |
подбор оборудования
до 90 дней