Внимание
Мы работаем в штатном режиме. Наши склады готовы поставлять оборудование клиентам из Российской Федерации несмотря на санкционные запреты ЕС и США. Оборудование в РФ ввозится легально благодаря новому законодательству с параллельным импортом. Звоните и уточняйте! Информация актуальна на 19.12.25В связи с участившимися случаями недобросовестной конкуренции обращаем ваше внимание, что мы не передаем персональные данные третьим лицам
Поиск по сайту
Межсетевой экран Palo Alto PA-5060
Почему нет цен?
Уточнить ценуГарантия до 5 лет
Диагностика перед отправкой
С нами выгодно и удобно!
- Поддержка персонального менеджера
- Партнёрские скидки до 70%
- Онлайн-кабинет гарантийного сервиса
Как купить?
Раз, два и все делаРассчитаем стоимость
Присылайте спецификацию для подбора и расчета стоимости оборудования
Привезём и подключим
Подключим и настроим оборудование в вашем офисе или ЦОДе
Характеристики
Отсрочка платежа
В зависимости от суммы поставляемого товара можем предоставить отсрочку платежа на срок от 5 до 90 дней. Условия отсрочки платежа рассматриваются индивидуально. Подробную информацию уточняйте у вашего менеджера.
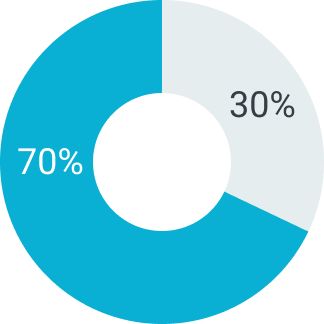
Первый платеж
Второй платеж
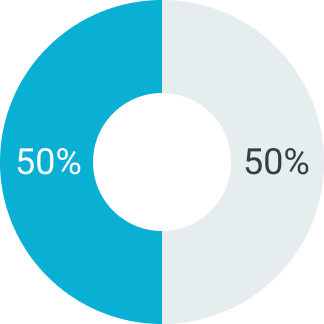
Первый платеж
Второй платеж
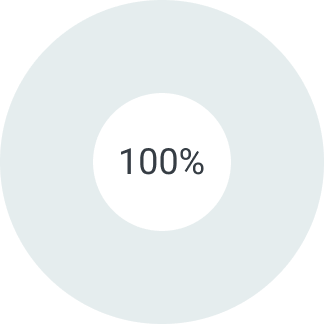
Первый платеж
Второй платеж
Описание
The Palo Alto Networks™ PA-5000 Series is comprised of three high-performance models, the PA-5060, the PA-5050 and the PA-5020, all of which are targeted at high-speed datacenter and Internet gateway deployments.
Use the PA-5060, PA-5050, and PA-5020 to safely enable applications, users, and content in the high-speed datacenter, large Internet gateway, service provider, and multi-tenant environments. Predictable throughput levels of up to 20 Gbps are achieved using dedicated, function-specific processing for networking, security, content inspection, and management.
Quick Specs
Table 1 shows the Quick Specs.
| Part number | PAN-PA-5060 |
| Description | Palo Alto Networks PA-5060, 20 Gbps firewall throughput, 10 Gbps threat prevention throughput |
| Firewall throughput (App-ID enabled) | 10 Gbps |
| Threat prevention throughput | 5 Gbps |
| IPSec VPN throughput | 4 Gbps |
| IPSec VPN tunnels/tunnel interfaces | 4,000 |
| Virtual routers | 125 |
| Security zones | 500 |
Product Details
Security Features1.Application Visibility
Port numbers, protocols, and IP addresses are useful for network devices, but they tell you nothing about what is on your network. Detailed information about the applications, users, and content traversing your network empowers you to quickly determine any risks they pose and quickly respond. Leveraging the rich context provided by Palo Alto Networks firewalls, our visualization, analysis, and reporting tools let you quickly learn more about activity on your network and analyze incidents from a current or comparative perspective.
2.User VisibilityAn integral component for secure application enablement policies.
Traditionally, security policies were applied based on IP addresses, but the increasingly dynamic nature of users and applications mean that IP addresses alone have become ineffective as a policy control element for safe application enablement. Palo Alto Networks next-generation firewalls integrate with a wide range of enterprise directories and terminal services offerings.
3.AntivirusNetwork-based Malware Protection.
The broadening use of social media, messaging and other non-work-related applications introduce a variety of vectors for viruses, spyware, worms and other types of malwares. Palo Alto Networks next-generation firewalls allow you to block unwanted applications with App-ID, and then scan allowed applications for malware.
4.Data Filtering & File BlockingThe application function level control, file blocking by type, and data filtering features of our next-generation firewalls allow you to implement a range of policies that help balance permitting the use of personal or non-work-related applications, with the business and security risks of unauthorized file and data transfer.
5.Modern Malware ProtectionWildFire: Protection from targeted and unknown threats.
Modern attackers are increasingly using targeted and new unknown variants of malware to sneak past traditional security solutions. To address this, Palo Alto Networks developed WildFire, which identifies new malware in minutes. By executing suspect files in a virtual environment and observing their behavior, Palo Alto Networks identifies malware quickly and accurately, even if the malware sample has never been seen before. Once a file is deemed malicious, WildFire automatically generates protections that are delivered to all WildFire subscribers within an hour of detection. A WildFire license provides your IT team with a wealth of forensics to see exactly who was targeted, the application used in the delivery, and any URLs that were part of the attack.
Networking Features
1.Decryption
Identify & Control Encrypted Traffic.
Take control of your SSL and SSH encrypted traffic and ensure it is not being used to conceal unwanted activity or dangerous content. Using policy-based decryption and inspection, you can confirm that SSL and SSH are being used for business purposes only, instead of to spread threats or unauthorized data transfer.
2.IPv6Safely enabling applications, users and content in IPv6 environments.
Our next-generation firewalls allow you to deploy consistent, safe application enablement policies across IPv6, IPv4 and mixed environments.
3.NetworkingOur flexible networking architecture includes dynamic routing, switching, and VPN connectivity, which enables you to easily deploy Palo Alto Networks next-generation firewalls into nearly any networking environment.
4.VPNStandards-based VPN Connectivity.
Secure site-to-site and remote user connectivity is a critical infrastructure component. Every Palo Alto Networks next-generation firewall platform allows you to easily and securely communicate between sites using standards-based IPSec VPN connections. Remote user communications are protected through a rich set of VPN features.
Compare to Similar Items
Table 2 shows the comparison.
| Model | PAN-PA-5060 | ||
| Firewall throughput (App-ID enabled) | 5 Gbps | 10 Gbps | 20 Gbps |
| Threat prevention throughput | 2 Gbps | 5 Gbps | 10 Gbps |
| IPSec VPN throughput | 2 Gbps | 4 Gbps | 4 Gbps |
| New sessions per second | 120,000 | 120,000 | 120,000 |
| Max sessions | 1,000,000 | 2,000,000 | 4,000,000 |
| IPSec VPN tunnels/tunnel interfaces | 2,000 | 4,000 | 8,000 |
| GlobalProtect (SSL VPN) concurrent users | 5,000 | 10,000 | 20,000 |
| SSL decrypt sessions | 15,000 | 45,000 | 90,000 |
| SSL Inbound Certificates | 100 | 300 | 1,000 |
| Virtual routers | 20 | 125 | 225 |
| Virtual systems (base/max2) | 10/20* | 25/125* | 25/225* |
| Security zones | 80 | 500 | 900 |
| Max. number of policies | 10,000 | 20,000 | 40,000 |
подбор оборудования
до 90 дней